Martin,
I was able to restore the wifi relay with these files. I see the field to add a custom NTP server - thank you.
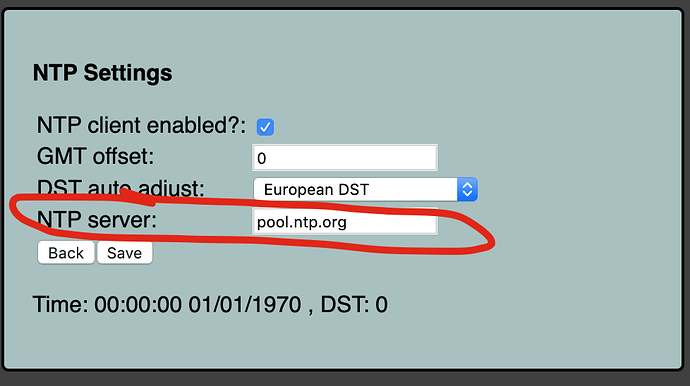
Unfortunately the device doesn’t update time at all.
It doesn’t initiate any NTP client connection at all - as inspected using packet capture (aka. wireshark). (This behaviour was the same in the previous v3190 version too, didn’t contact pool.ntp.org at all)
See below a capture made on the firewall itself, straight after powering on the unit:
19:29:45.197392 dc:4f:22:40:ba:a5 > ff:ff:ff:ff:ff:ff Null Supervisory, Receiver not Ready, rcv seq 64, Flags [Poll], length 42
19:29:45.222707 IP 0.0.0.0.68 > 255.255.255.255.67: UDP, length 308
19:29:45.222843 IP 172.22.215.254.67 > 172.22.215.18.68: UDP, length 300
19:29:45.228543 IP 0.0.0.0.68 > 255.255.255.255.67: UDP, length 308
19:29:45.228659 IP 172.22.215.254.67 > 172.22.215.18.68: UDP, length 300
19:29:45.233869 ARP, Request who-has 172.22.215.18 tell 0.0.0.0, length 42
19:29:45.572315 ARP, Request who-has 172.22.215.18 tell 0.0.0.0, length 42
19:29:46.072586 ARP, Request who-has 172.22.215.18 tell 172.22.215.18, length 42
19:29:46.780197 ARP, Request who-has 172.22.215.60 tell 172.22.215.18, length 42
19:30:13.109514 dc:4f:22:40:ba:a5 > ff:ff:ff:ff:ff:ff Null Supervisory, Receiver not Ready, rcv seq 64, Flags [Poll], length 42
19:30:13.126688 IP 0.0.0.0.68 > 255.255.255.255.67: UDP, length 308
19:30:13.126807 IP 172.22.215.254.67 > 172.22.215.18.68: UDP, length 300
19:30:13.133956 IP 0.0.0.0.68 > 255.255.255.255.67: UDP, length 308
19:30:13.134037 IP 172.22.215.254.67 > 172.22.215.18.68: UDP, length 300
19:30:13.136552 ARP, Request who-has 172.22.215.18 tell 0.0.0.0, length 42
19:30:13.502191 ARP, Request who-has 172.22.215.18 tell 0.0.0.0, length 42
19:30:14.002155 ARP, Request who-has 172.22.215.18 tell 172.22.215.18, length 42
19:30:14.741276 ARP, Request who-has 172.22.215.60 tell 172.22.215.18, length 42
172.22.215.254 is the gateway/dhcp/ntp server. 172.22.215.18 is the wifi relay. As you can see, only DHCP messages are initiated by the relay, nothing else.
Also the other issue is still present: If I change the name of the relay, it won’t connect to the wifi after reboot. Need to set it to AP mode with the button, enter network key again and after that, it’s going to be fine.
Time is always 00:00:00 01/01/1970 , DST: 0 and also Uptime: 0 days, 0 hours, 0 minutes, 0 seconds doesn’t increase.
GMT offset and DST auto adjust are not saved.
(these were all present in v3190 too!)